Machine Learning: Its Role in Cybersecurity
In today’s world, it is non-viable to work with cybersecurity technology without working closely with machine learning and artificial intelligence. Machine learning is a term used side by side with artificial intelligence and deep learning in most cases. We shall be learning what this “Machine Learning” is and how it can impact cybersecurity today. What […]
The Deepfake Technology: A Rising Cybersecurity Threat

What Is a Deepfake? A deepfake is a technology that involves creating fake content and narratives such as a fake image, audio or video of a person. The term “deepfake” is a combination of the words “deep” and “fake”. Deep means deep learning – a form of artificial intelligence (AI), while fake means unreal. Therefore, […]
Crypto is Cybercrime’s Currency of Choice

While 2021, unfortunately, played host to a wide variety of threats, it’s unlikely any factor will feature more prominently than cryptocurrency in the years to come. Two types of attacks leverage cryptocurrency directly: extortion and cryptojacking. Before cryptocurrency, cybercriminals had to work much for far lower pay. Turning stolen personal information or credit cards into […]
Web App & API Security Needs an Overhaul: Here’s How

In today’s contemporary society, applications are critical for doing business. They are also the weakest links in the security chain of many organizations. Many APIs, by design, continue to expose the personally identifiable information of customers, employees and contractors. OWASP (Open Web Application Security Project) notes on its API Security Project homepage: “By nature, APIs […]
Google Issues Warning on State of the Art Predator Spyware

As part of its continuous efforts to make Android smartphones more secure, Google’s Threat Analysis Group TAG monitors for zero-day vulnerabilities that can be exploited by hackers and other threat actors. Recently TAG has issued a warning about a potent PREDATOR spyware that is targeting Android smartphones globally. These vulnerabilities represent a substantial threat because […]
What is Wi-Fi Wardriving and How Can you Protect Yourself and Business?

Wi-Fi Wardriving refers to the act of hackers who drive around in cars or other automobiles looking to find which Wi-Fi routers are unsecured and hence most/more vulnerable to hacking attempts in a specific location/area. These hackers employ equipment and software to detect the presence of unprotected networks and map the wireless access points. The […]
Setting Up Digital Legacy Contact on iPhone
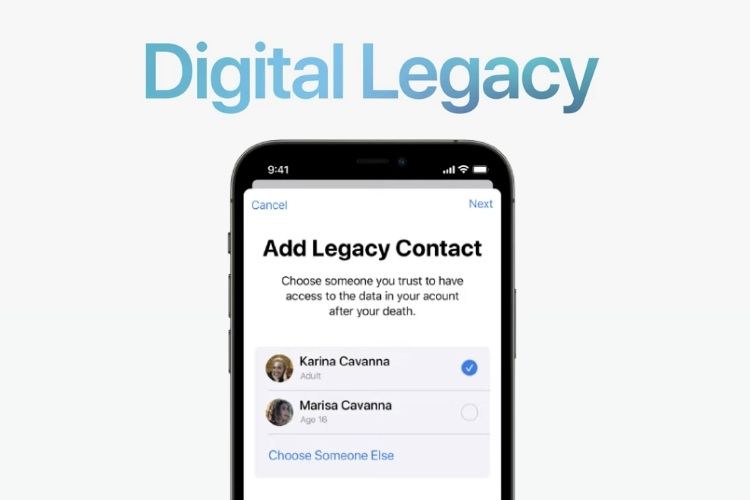
A Legacy Contact lets users designate someone who will have access to their data in their Apple account after their demise. Once someone has been designated as the Apple ID’s Legacy contact, that individual can request access to the data after the account owner has died. What type of data can Legacy contacts can request? […]
How to Setup Mouse for Left-handed Users in Windows 11

If you are left-handed, you have probably had problems using a mouse on Windows laptops or PCs. While Windows 11 can detect a connection and setup a mouse automatically, it does so by default for right-handed users, which means the left click will be configured as the main key. If you are left-handed and prefer […]
How to Secure Corporate Emails from Malicious Attacks

In the contemporary times, the Email is amongst the most used tools for personal and corporate communication. However, email is inherently insecure. When you send an email, it is in plain text and is saved on the computer of the recipient. There is no guarantee that your communication will be secure either in transit or […]
Safe Guarding Personal & Critical Data Using Passwords

Passwords are not a particularly secure method of protection, and in a world where multifactor authentication is becoming the norm, talking about password hygiene seems a little outdated. However, according to the Verizon 2021 Data Breach Investigations Report, passwords are the route to data breaches in 61 percent of incidents. In an ideal world, and […]